路由技术IPV6实验
路由技术IPV6隧道实验,拓扑配置如下:
GRE(通用路由协议封装)规定了用一种网络协议去封装另一种网络协议的方法。下面是IPV6-over-IPV4GRE隧道配置实验。
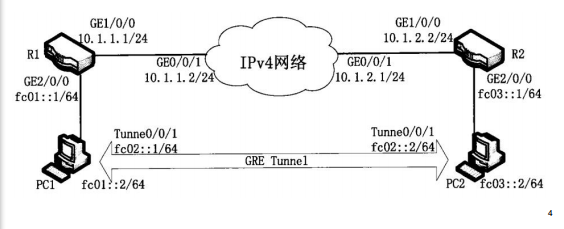
第一步:配置个各设备IP:R1、R2、及各PC。
system-view
[Huawei]sysname R1
[R1]interface GigabitEthernet 1/0/0
[R1-GigabitEthernet1/0/0]ip address 10.1.1.1 24
[R1-GigabitEthernet1/0/0]quit
[R1]ipv6 //全局启用IPV6
[R1]interface GigabitEthernet 2/0/0
[R1-GigabitEthernet2/0/0]ipv6 enable //接口启用IPV6
[R1-GigabitEthernet2/0/0]ipv6 add fc01::1 64
[R1-GigabitEthernet2/0/0]quit
system-view
[Huawei]sysname R2
[R2]interface GigabitEthernet 1/0/0
[R2-GigabitEthernet1/0/0]ip add 10.1.2.2 24
[R2-GigabitEthernet1/0/0]quit
[R2]ipv6
[R2]interface GigabitEthernet 2/0/0
[R2-GigabitEthernet2/0/0]ipv6 enable
[R2-GigabitEthernet2/0/0]ipv6 add fc03::1 64
[R2-GigabitEthernet2/0/0]quit
第二部:配置R1、R2的IPV4静态路由。
[R1]ip route-static 10.1.2.2 255.255.255.0 10.1.1.2
[R2]ip route-static 10.1.1.1 255.255.255.0 10.1.2.1
第三步:配置R1、R2的Tunnel接口。
[R1]interface tunnel 0/0/1 //进入隧道口
[R1-Tunnel0/0/1]tunnel-protocol gre //隧道协议GRE
[R1-Tunnel0/0/1]ipv6 enable
[R1-Tunnel0/0/1]ipv6 address fc02::1 64
[R1-Tunnel0/0/1]source 10.1.1.1 //源IP地址
[R1-Tunnel0/0/1]destination 10.1.2.2 //目的IP地址
[R1-Tunnel0/0/1]quit
[R2]interface tunnel 0/0/1
[R2-Tunnel0/0/1]tunnel-protocol gre
[R2-Tunnel0/0/1]ipv6 enable
[R2-Tunnel0/0/1]ipv6 address fc02::2 64
[R2-Tunnel0/0/1]source 10.1.2.2
[R2-Tunnel0/0/1]description 10.1.1.1
[R2-Tunnel0/0/1]quit
第四步:配置R1、R2的Tunnel静态路由。
[R1]ipv6 route-static fc03::1 64 tunnel 0/0/1
[R2]ipv6 route-static fc01::1 64 tunnel 0/0/1
第五步:验证检查配置结果
[R2]ping 10.1.1.1
[R2]ping ipv6 fc01::1
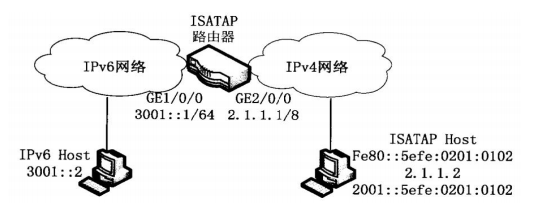
路由技术IPV6的ISATAP隧道实验如下。
第一步:配置路由器接口IP、双栈。
system-view
[Huawei]sysname Router
[Router]ipv6
[Router]interface GigabitEthernet 1/0/0
[Router-GigabitEthernet1/0/0]ipv6 enable
[Router-GigabitEthernet1/0/0]ipv6 address 3001::1 64
[Router-GigabitEthernet1/0/0]quit
[Router]interface GigabitEthernet 2/0/0
[Router-GigabitEthernet2/0/0]ip address 2.1.1.1 255.0.0.0
[Router-GigabitEthernet2/0/0]quit
[Router]interface tunnel 0/0/2
[Router-Tunnel0/0/2]tunnel-protocol ipv6-ipv4 isatap //隧道协议ISATAP
[Router-Tunnel0/0/2]ipv6 enable
[Router-Tunnel0/0/2]ipv6 address 2001:: 64 eui-64
[Router-Tunnel0/0/2]source GigabitEthernet 0/0/2
[Router-Tunnel0/0/2]undo ipv6 nd ra halt //发送RA消息
第二部:配置ISATAP主机。
C:\>netsh interface ipv6 isatap set router 2.1.1.1
C:\>netsh interface ipv6 isatap set router 2.1.1.1 enabled
第三步:配置IPV6网络主机。
C:\>netsh interface ipv6 set route 2001::/64 3001::1
路由器技术IPSec实验
路由技术IPSec实验,拓扑配置如下。
某公司总部和分支机构构成,通过IPSec VPN实现网络安全,具体机构和配置如下。
第一步:配置R1、R2的接口IP和静态路由。
system-view
[Huawei]sysname R1
[R1]interface GigabitEthernet 1/0/0
[R1-GigabitEthernet1/0/0]ip address 168.1.1.1 24
[R1-GigabitEthernet1/0/0]quit
[R1]interface GigabitEthernet 2/0/0
[R1-GigabitEthernet2/0/0]ip address 172.22.1.100 24
[R1-GigabitEthernet2/0/0]quit
[R1]ip route-static 167.1.1.1 24 168.1.1.2
[R1]ip route-static 172.22.2.0 24 168.1.1.2
system-view
[Huawei]sysname R2
[R2]interface GigabitEthernet 1/0/0
[R2-GigabitEthernet1/0/0]ip address 167.1.1.1 24
[R2-GigabitEthernet1/0/0]quit
[R2]interface GigabitEthernet 2/0/0
[R2-GigabitEthernet2/0/0]ip address 172.22.2.100 24
[R2-GigabitEthernet2/0/0]quit
[R2]ip route-static 168.1.1.0 24 167.1.1.2
[R2]ip route-static 172.22.1.0 24 167.1.1.2
第二部:配置R1、R2的ACL保护数据流。
[R1]acl number 3101
[R1-acl-adv-3101]rule permit ip source 172.22.1.0 0.0.0.255 destination172.22.2.
[R2]acl number 3101
[R2-acl-adv-3101]rule permit ip source 172.22.2.0 0.0.0.255 destination 172.22.1.0 0.0.0.255
第三步:配置R1、R2的IPSec安全协议。
[R1]ipsec proposal tran1 //创建IPSes安全提议
[R1-ipsec-proposal-tran1]esp authentication-algorithm sha2-256
[R1-ipsec-proposal-tran1]esp encryption-algorithm aes-128
[R2]ipsec proposal tran1 //ESP采用SHA认证 SEA加密
[R2-ipsec-proposal-tran1]esp authentication-algorithm sha2-256
[R2-ipsec-proposal-tran1]esp encryption-algorithm aes-128
第四步:配置R1、R2的IKE对等体。
[R1]ike peer spub
[R1-ike-peer-spub]undo version 2
[R1-ike-peer-spub]ike-proposal 5
[R1-ike-peer-spub]pre-shared-key cipher huawei
[R1-ike-peer-spub]remote-address 167.1.1.1
[R2]ike peer spub
[R2-ike-peer-spub]undo version 2
[R2-ike-peer-spub]ike-proposal 5
[R2-ike-peer-spub]pre-shared-key cipher huawei
[R2-ike-peer-spub]remote-address 192.168.1.1
第五步:配置R1、R2的安全策略组。
[R1]ipsec policy map1 10 isakmp
[R1-ipsec-policy-isakmp-map1-10]ike-peer spub
[R1-ipsec-policy-isakmp-map1-10]proposal tran1
[R1-ipsec-policy-isakmp-map1-10]security acl 3101
[R2]ipsec policy map1 10 isakmp
[R2-ipsec-policy-isakmp-map1-10]ike-peer spub
[R2-ipsec-policy-isakmp-map1-10]proposal tran1
[R2-ipsec-policy-isakmp-map1-10]security acl 3101
第六步:安全策略组应用R1、R2的接口上。
[R1]interface GigabitEthernet 1/0/0
[R1-GigabitEthernet1/0/0]ipsec policy map1
[R2]interface GigabitEthernet 1/0/0
[R2-GigabitEthernet1/0/0]ipsec policy map1
第七步:测试配置验证结果。
display ipsec statistics
display ike sa
display ipsec proposal

We totally concur with your insights. Your post has given me a lot of fresh ideas. Thanks for sharing.
Your article gives a lot of helpful information. I found it very useful. Thanks for posting such a detailed post.